[rank_math_breadcrumb]
Protect Your Fleet of Devices With Secure IT Assets Lifecycle Management
Manage and protect your sensitive data and stay in compliance with the highest industry standards throughout the lifecycle of your device.

The Lingering Security Threats
- Difficulty ensuring timely application of patches and updates across diverse IT environments, leading to increased vulnerability to cyber threats
- You need automated patch management tools and services to ensure the timely application of patches and updates across diverse IT environments. Risk-based patch prioritization based on vulnerability severity and impact assessments. Conduct regular vulnerability scans and threat intelligence analysis to proactively identify and mitigate potential cyber threats.
- Challenges in protecting sensitive data stored on IT assets from unauthorized access and data breaches throughout the asset lifecycle.
- Partner with ITALM company that provides comprehensive data security solutions, including encryption, access controls, and data loss prevention (DLP) tools, to protect sensitive data throughout the asset lifecycle. Offer security audits and penetration testing.
- Struggle to ensure IT asset management practices comply with industry regulations and standards such as GDPR, HIPAA, PCI DSS, leading to potential legal and regulatory penalties.
- Follow procedures that align with industry regulations and standards such as GDPR, HIPAA, PCI DSS. Offer compliance assessment services, audit trails, and reporting capabilities to ensure compliance with regulatory requirements. At Unduit we provide remediation support and guidance to address non-compliance issues and mitigate legal and regulatory risks.
- Difficulty tracking the movement and usage of assets across different departments or locations, leading to gaps in security controls and compliance.
- You need asset tagging, labeling, and tracking solutions to track assets across different locations and departments accurately. Get asset-tracking solutions with barcode or RFID technology to track the movement and usage of assets effectively. Implement asset lifecycle management processes and audits to track assets from procurement to disposal accurately.
- Challenges in conducting regular risk assessments to identify potential threats and vulnerabilities associated with IT assets, including legacy systems or outdated software that may pose security risks.
- Develop risk mitigation strategies, action plans, and security controls to address identified risks effectively. Get risk assessment reports, recommendations, and ongoing risk management support to mitigate security risks throughout the asset lifecycle.
Quantifiable Results – Scalable Services
Get measurable results within weeks of partnering with Unduit.
- Compliance Management: Get 100% compliance with industry regulations such as GDPR, HIPAA, PCI DSS for clients partnering with Unduit.
- Secure Platform: 100% secure platform because of the frequent updates and security patches.
- Assets Tracking: Get 100% transparent and full visibility into who is handling your assets and where the assets are located.
- Certified Data Erasure: 100% secure data erasure. Get certified data erasure for your recycled assets.

No Detail is Overlooked
Comprehensive Hardware Evaluation
- Our team of expert technicians conducts thorough hardware audits, leaving no stone unturned.
- We meticulously locate and identify all hardware equipment within your company, examining each component to ensure it meets your business's procedures and standards.
- From servers and workstations to networking devices and peripherals, we assess the adequacy and effectiveness of your hardware infrastructure.
Benefits of Partnering With Unduit.
Vulnerability Scans and Threat Analysis
Get regular vulnerability scans and threat analysis for your devices.
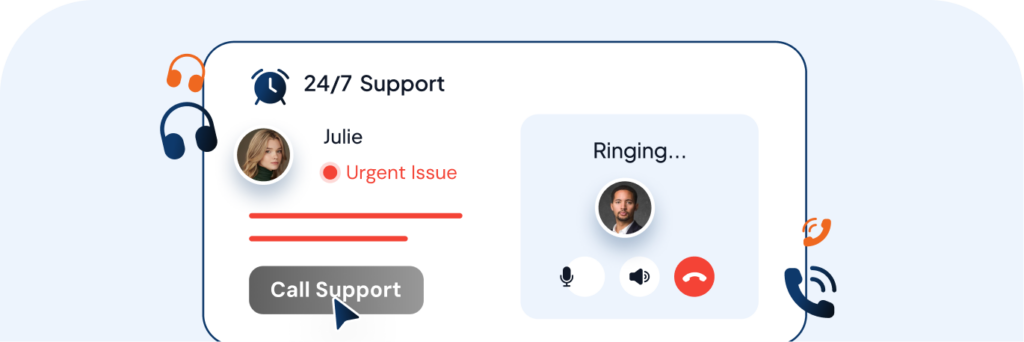
24/7 Support
Expert suggestions around the clock and learn how to protect your fleet
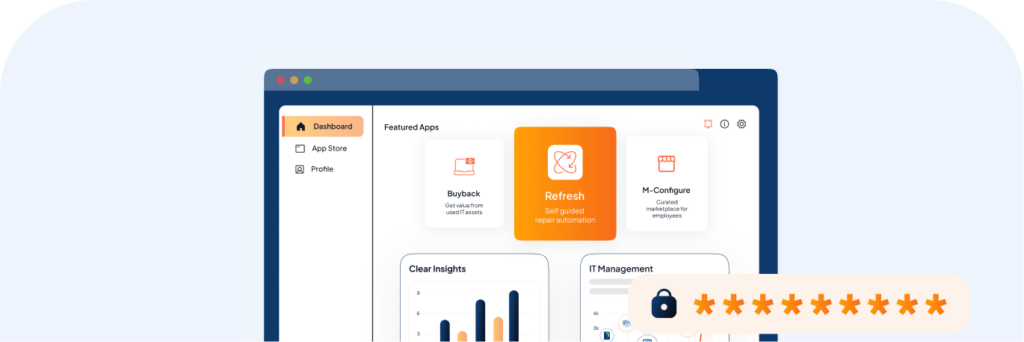
Secure platform
We frequently update our platform and apps to eliminate any security threats.
Interested in boosting your IT ROI and Security?
Join over 200+ enterprises already using Unduit
Interested in boosting your IT ROI and Security?
Join over 200+ enterprises already using Unduit